HIPAA Risk Analysis
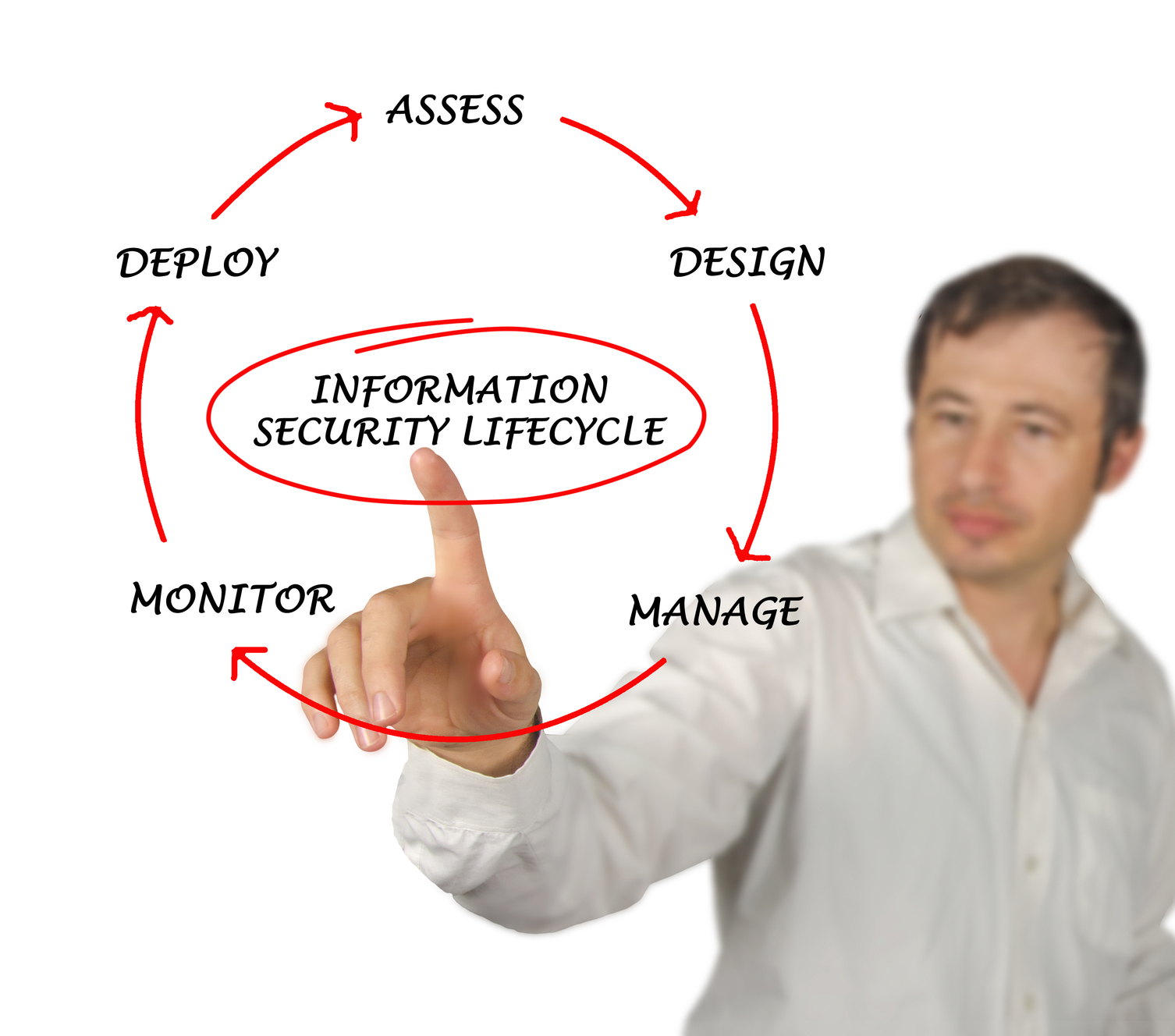
Conducting a risk analysis is the first step in identifying and implementing safeguards that comply with and carry out the standards and implementation specifications in the HIPAA Security Rule. We will provide this service to you. All electronic protected health information created, received, maintained or transmitted by an organization is subject to the Security Rule. The Security Rule requires entities to evaluate risks and vulnerabilities in their environments and to implement reasonable and appropriate security measures to protect against anticipated threats or hazards to the security or integrity of electronic protected health information. Methods will vary depending on size, complexity, and capabilities of an organization. A risk analysis is part of the compliance process and is a critical factor in assessment of your organization's compliance. Cybersecurity risks continue to have critical impacts on overall risk modeling, assessments and mitigation efforts. With increased cybersecurity incidents, increased lawsuits related to cybersecurity vulnerabilities and debates over who is ultimately responsible for protecting health information, personal information, and consumer information are commonplace. Any cloud provider or third party a business uses should be scrutinized and have clearly laid out policies and responsibilities of each party involved. Any cloud provider should sign a BA Agreement, and any reputable cloud provider should be able to pass a SOC 2 audit.


